一、基本情况
KE协议是一份符合因特网协议安全(IPSec)标准的协议。因特网密钥交换协议是结合了两个早期的安全协议而生成的综合性协议。
二、漏洞描述
Windows IKE 协议扩展存在远程代码执行漏洞,此漏洞允许远程攻击者在系统上执行任意代码。IKEEXT 在处理 IKEv1数据包时,没有对用户输入进行充分验证,未经身份认证的远程攻击者可通过向受影响的系统发送特制的 IKEv1数据包触发漏洞,并执行任意代码。
三、影响范围
Windows Server 2022
Windows 10 Version 21H1 for 32-bit Systems
Windows 10 Version 21H1 for ARM64-based Systems
Windows 10 Version 21H1 for x64-based Systems
Windows Server 2019 (Server Core installation)
Windows Server 2019
Windows 10 Version 1809 for ARM64-based Systems
Windows 10 Version 1809 for x64-based Systems
Windows 10 Version 1809 for 32-bit Systems
Windows Server 2012 R2 (Server Core installation)
Windows Server 2012 R2
Windows Server 2012 (Server Core installation)
Windows Server 2012
Windows Server 2008 R2 for x64-based Systems Service Pack 1 (Server Core installation)
Windows 10 Version 21H2 for x64-based Systems
Windows 10 Version 21H2 for ARM64-based Systems
Windows 10 Version 21H2 for 32-bit Systems
Windows 11 for ARM64-based Systems
Windows 11 for x64-based Systems
Windows 10 Version 20H2 for ARM64-based Systems
Windows 10 Version 20H2 for 32-bit Systems
Windows 10 Version 20H2 for x64-based Systems
Windows Server 2022 Azure Edition Core Hotpatch
Windows Server 2022 (Server Core installation)
Windows Server 2008 R2 for x64-based Systems Service Pack 1
Windows Server 2008 for x64-based Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for x64-based Systems Service Pack 2
Windows Server 2008 for 32-bit Systems Service Pack 2 (Server Core installation)
Windows Server 2008 for 32-bit Systems Service Pack 2
Windows RT 8.1
Windows 8.1 for x64-based systems
Windows 8.1 for 32-bit systems
Windows 7 for x64-based Systems Service Pack 1
Windows 7 for 32-bit Systems Service Pack 1
Windows Server 2016 (Server Core installation)
Windows Server 2016
Windows 10 Version 1607 for x64-based Systems
Windows 10 Version 1607 for 32-bit Systems
Windows 10 for x64-based Systems
Windows 10 for 32-bit Systems
四、修复建议
一、自查检测方案
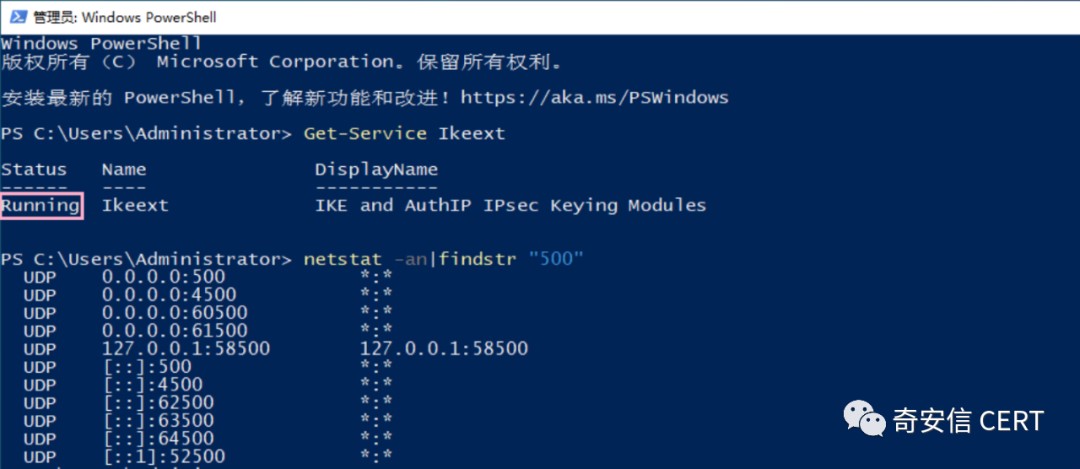
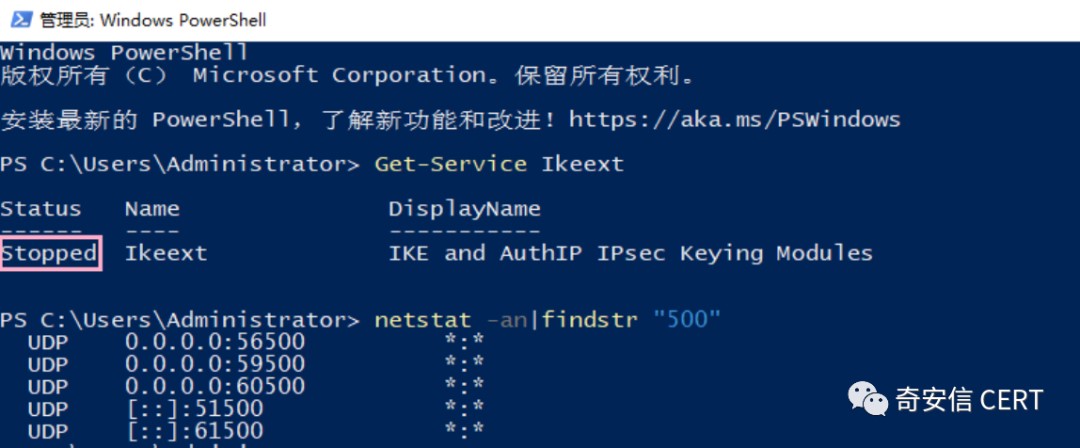
只有运行 IKE 和 AuthIP IPsec 密钥模块的系统才容易受到这种攻击,用户可通过PowerShell 命令Get-Service Ikeext 查看该服务运行的状态:
开启示例:
未开启示例:
详情请参考:https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-34721
二、修复缓解措施
1、若非必须,不要启用 IPSec 服务;
2、限制未知来源对 500、4500 端口的访问;
三、修复解决方案(含漏洞补丁)
微软官方已发布安全更新,系统可自动更新。若不能自动更新,用户可参考以下链接手动打补丁:https://msrc.microsoft.com/update-guide/en-US/vulnerability/CVE-2022-34721
五、参考链接
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2022-34721
https://www.cyfirma.com/outofband/windows-internet-key-exchange-ike-remote-code-execution-vulnerability-analysis